What’s the Buffer Overflow vulnerability?
Buffer overflow vulnerability is a type of security vulnerability that can allow an attacker to execute malicious code on a system or gain…
Buffer overflow vulnerability is a type of security vulnerability that can allow an attacker to execute malicious code on a system or gain unauthorized access to sensitive information. This vulnerability is caused when a program tries to write data to a buffer that is not large enough to hold the data.
When this happens, the data overflows the buffer and is written to adjacent memory locations, potentially overwriting data from other parts of the program. This can cause the program to behave unexpectedly or crash and, in some cases, allow an attacker to execute arbitrary code.
At a low level, a buffer overflow occurs when a program attempts to write data to a memory location outside the buffer’s bounds. In many programming languages, including C and C++, buffers are implemented as arrays of bytes allocated in memory. When data is written to a buffer, the program checks to ensure that the data will fit within the allocated buffer size. If the data is too large, the program will overwrite the adjacent memory locations, which can cause undefined behaviour.
For example, consider the following C code:
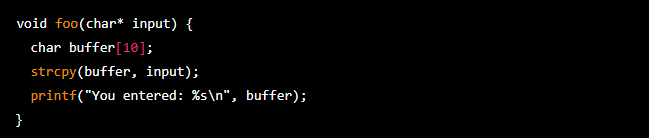
In this code, the foo function takes a string as input and copies it into a buffer of only 10 bytes. If the input string is longer than 10 bytes, the strcpy function will overwrite adjacent memory locations, potentially causing the program to crash or behave unpredictably. An attacker could exploit this vulnerability by crafting an input string that contains malicious code, which would be executed when the program overwrites the adjacent memory locations.
To prevent buffer overflow vulnerabilities, there are several techniques that software developers can use.
One approach is to use programming languages that provide built-in bounds checking, such as Java, Python, or Rust. These languages automatically check the size of buffers and prevent overflows. However, these languages may only be suitable for some applications, and developers may need other techniques to prevent buffer overflows.
Another approach is using code analysis tools to detect potential buffer overflow vulnerabilities. These tools can identify vulnerable code and suggest changes to prevent overflows. For example, static analysis tools can examine the source code of a program to identify potential buffer overflows. In contrast, dynamic analysis tools can monitor the program’s behaviour at runtime to detect overflows.
In addition, developers can implement defensive programming techniques to prevent buffer overflows. For example, developers can validate user input to ensure that it is within the bounds of the buffer, or they can restrict the size of buffers to prevent overflows. Developers can also use secure coding practices, such as avoiding unsafe functions like strcpy and gets, which do not perform bounds checking.
Buffer overflow vulnerabilities can be a severe security risk for software applications. However, there are several techniques that software developers can use to prevent these vulnerabilities. By using programming languages with built-in bounds checking, code analysis tools, defensive programming techniques, and secure coding practices, developers can help ensure the security and reliability of their software applications.
Follow me on Medium and LinkedIn.
I am looking forward to hearing from you!
All the best,
Luis Soares
CTO | Head of Engineering | Blockchain & Fintech SME | Startup Advisor | Board Member
#securecoding #security #bestpractices #cybersecurity #safe #softwareengineering #softwaredevelopment #coding #software



