Understanding Microservice Meshes: Architecture, Operation, and Examples
A service mesh is a dedicated infrastructure layer that facilitates service-to-service communications in a microservices architecture…
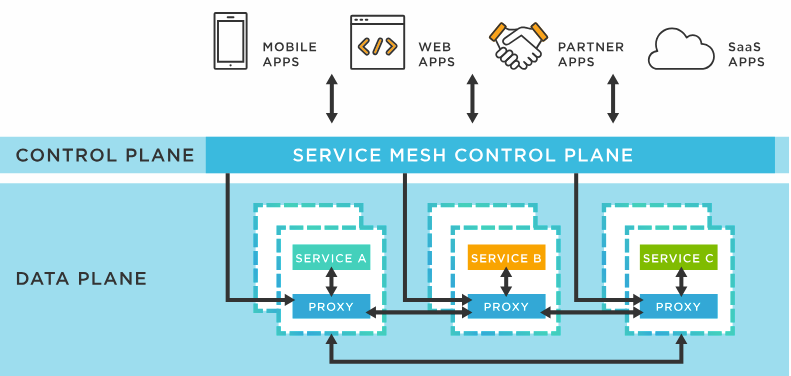
A service mesh is a dedicated infrastructure layer that facilitates service-to-service communications in a microservices architecture, handling service discovery, load balancing, failure recovery, metrics, and monitoring. By abstracting these functionalities, a service mesh allows developers to focus on business logic in their services, enhancing their productivity.
As microservices proliferate, coordinating, managing, and ensuring seamless communication between them becomes a complex task. The service mesh addresses these challenges by providing a unified, application-agnostic framework that simplifies and standardizes inter-service communication, making it robust, secure, and observable.
How Service Meshes Work
Service meshes operate at the application network level. This model decouples the networking logic from the application logic, thus avoiding a tangled mess of point-to-point communication paths.
Service meshes can be divided into two main components: the data and control planes.
Data Plane
The data plane, often implemented with sidecar proxies, is responsible for the direct routing, control, and transformation of network packets. When a service wants to communicate with another, it sends the request to its sidecar proxy, which handles the communication with the corresponding proxy of the target service. The sidecar proxy pattern helps developers ensure that the infrastructure handling service-to-service communication is separate from the services themselves.
Control Plane
The control plane, on the other hand, is responsible for controlling the behaviour of the data plane. It configures the proxies and extracts telemetry data from them, which it then uses to provide observability. The control plane provides a bird's-eye view of the entire mesh and is crucial for managing and monitoring the data plane.
Benefits of Service Meshes
Service meshes provide numerous benefits:
- Observability: Service meshes provide in-depth observability into the service ecosystem, providing critical insights into performance, failures, and network behaviour. This feature helps developers and operators understand the interdependencies between services, detect anomalies, and troubleshoot issues.
- Security: Service meshes enhance security by enforcing access policies, performing traffic encryption, and ensuring secure service-to-service communication.
- Traffic Management: They provide advanced traffic management capabilities, such as load balancing, routing, and circuit breaking.
- Resiliency: Service meshes improve the system's resiliency by providing inbuilt failure recovery features, including retries, timeouts, and failovers.
- Tracing and Monitoring: They support distributed tracing and provide real-time monitoring, enhancing the visibility of service performance and interaction patterns.
Popular Service Mesh Examples
Istio
Istio is a popular open-source service mesh that provides a robust way to connect, manage, and secure microservices. Istio integrates with Kubernetes and runs in various environments, including on-premises, cloud-hosted, in Kubernetes containers, and services running on virtual machines.
Linkerd
Linkerd is a light, fast, and security-focused service mesh for Kubernetes. It features a simple and straightforward setup, with robust capabilities like load balancing, retries, timeouts, and a dashboard for observability.
Consul Connect
Consul Connect, developed by HashiCorp, provides service-to-service connection authorization and encryption using mutual Transport Layer Security (TLS). With its service discovery and health-checking features, Consul Connect is a powerful tool for building a secure, agile, and resilient microservice architecture.
Advanced Service Mesh Features
Beyond the fundamental capabilities, many service meshes offer advanced features such as:
- Canary Releases and Blue/Green Deployments: Service meshes allow developers to gradually roll out service changes, reducing the risk of system-wide failures caused by problematic updates. They can split traffic between different service versions, helping teams to test and roll out new features gradually or switch between different environments smoothly.
- Rate Limiting: This feature helps protect your services from being overwhelmed by too many requests. It allows developers to limit the number of requests a service can make or accept, ensuring the service is manageable.
- Service Mesh Interface (SMI): SMI is a standard interface for service meshes on Kubernetes. It defines a set of common, portable APIs that provide interoperability between different service mesh technologies. This means that applications can change the service mesh underneath without any code changes.
- Fault Injection: Service meshes allow developers to inject faults into the system intentionally, simulating failures of services or networks. This functionality helps in testing the system's resilience and failure recovery mechanisms.
Practical Example: Implementing Istio in a Microservices Architecture
Istio leverages an extended version of the Envoy proxy, a high-performance, open-source edge and service proxy that makes the network transparent to applications. This guide will walk you through the process of integrating Istio into your microservice applications.
Istio Installation
The first step is to install Istio on your Kubernetes cluster. There are a few different ways to do this, but the simplest is to use the Istio command-line tool, istioctl. You can download the latest Istio release from the official Istio website.
- After downloading and extracting the package, navigate to the directory in your terminal and add the
istioctlclient to your PATH:
cd istio-<version>
export PATH=$PWD/bin:$PATH2. You can now install Istio using the istioctl install command. This will install Istio using the default profile, which is suitable for most use cases:
istioctl install3. Verify the installation by checking that the necessary Istio pods are running in the istio-system namespace:
kubectl get pods -n istio-systemDeploying Sample Application
To understand how Istio works, let’s deploy a sample application. We’ll use the Bookinfo application provided by Istio. It comprises four microservices and illustrates the power of Istio’s features.
- To deploy the application, use the
kubectl applycommand:
kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml2. Confirm that all services and pods are correctly defined and running:
kubectl get services
kubectl get podsEnabling Istio on Services
We need to enable sidecar injection to make our application part of the Istio service mesh. Istio uses sidecar proxies to enhance each service in the mesh.
- Label the namespace so to inject Envoy sidecar proxies automatically:
kubectl label namespace default istio-injection=enabled2. Redeploy the application:
kubectl delete -f samples/bookinfo/platform/kube/bookinfo.yaml
kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml3. Check that each pod in your application now has two containers. The second container is the Envoy proxy:
kubectl get podsConfiguring Traffic Routing
To control traffic routing in Istio, we use a VirtualService configuration. Let's create one for our Bookinfo application.
- Apply a default destination rule:
kubectl apply -f samples/bookinfo/networking/destination-rule-all.yaml2. Now, let’s route all traffic to the v1 version of each microservice. Apply the VirtualService:
kubectl apply -f samples/bookinfo/networking/virtual-service-all-v1.yaml3. Verify that all traffic is routed to v1 of each service:
kubectl get virtualservices -o yamlIn the output, you should see that traffic is being routed to v1 for all services.
Implementing a Canary Release
One powerful feature of Istio is the ability to implement a canary release. We’ll route a small percentage of traffic to v2 of the reviews service.
- Update the VirtualService configuration:
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: reviews
spec:
hosts:
- reviews
http:
- route:
- destination:
host: reviews
subset: v1
weight: 90
- destination:
host: reviews
subset: v2
weight: 102. Apply the new VirtualService:
kubectl apply -f <filename.yaml>Now, approximately 10% of traffic should be routed to the v2 of the reviews service.
Istio offers many capabilities for managing, observing, and securing microservices communication in distributed applications.As always, the official Istio documentation is the definitive source of information for deeper exploration.
Future of Service Meshes
Service meshes, in their relatively short existence, have profoundly impacted how microservices are developed and managed. As more organizations adopt microservices and containers, the need for robust service mesh solutions will continue to grow.
Service mesh technology will likely continue to evolve, incorporating AI and machine learning for advanced traffic management, anomaly detection, and automated remediation of issues. Furthermore, standardization efforts like the Service Mesh Interface will increase interoperability, simplifying adoption and migration between different service meshes.
Stay tuned, and happy coding!
Visit my Blog for more articles, news, and software engineering stuff!
Follow me on Medium, LinkedIn, and Twitter.
Check out my most recent book — Application Security: A Quick Reference to the Building Blocks of Secure Software.
All the best,
Luis Soares
CTO | Head of Engineering | Rust | Java | Solidity | Golang | Smart Contracts | Web3 | Cyber Security
#servicemesh #mesh #microservices #eventdriven #architecture #service #api #programming #language #softwaredevelopment #coding #software #safety #development #building #architecture #data #network #communication #communications #infrastructure #networking



