Kademlia, Chord, and Pastry: Understanding Distributed Hash Table Algorithms
Distributed Hash Tables (DHTs) are a class of decentralized distributed systems that provide a lookup service similar to hash tables, in…
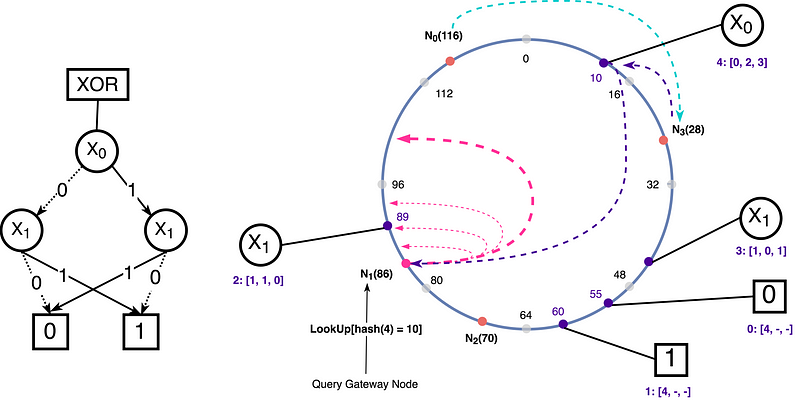
Distributed Hash Tables (DHTs) are a class of decentralized distributed systems that provide a lookup service similar to hash tables, in which key-value pairs can be inserted, deleted, and retrieved.
DHTs are the foundation of many large-scale peer-to-peer (P2P) networks and are used in applications such as file-sharing systems, content distribution networks, and domain name systems.
Three of the most popular and widely studied DHT algorithms are Kademlia, Chord, and Pastry.
This article will comprehensively explain each, detailing their inner workings, advantages, and drawbacks.
Let's dive right in!
Kademlia
Kademlia was a P2P DHT protocol Petar Maymounkov and David Mazières proposed in 2002. It is based on the XOR metric, enabling it to achieve low-latency routing, logarithmic state, and lookup complexity.
Kademlia's main features are:
a. NodeID and Key Space: Kademlia represents nodes and keys with unique, fixed-length identifiers (NodeIDs and KeyIDs) in a binary space. The XOR distance between NodeIDs is used as a proximity metric.
b. Routing Table: Each node maintains a routing table consisting of k-buckets, where each k-bucket corresponds to a different range of distances from the node. The k-buckets store the contact information of the k-closest nodes in that distance range.
c. Lookup Algorithm: The process involves iterative queries to nodes progressively closer to the target KeyID. Each query returns a set of closer nodes, which are then used in subsequent queries.
d. Data Storage and Retrieval: Data is stored as key-value pairs on the k closest nodes to the KeyID. A lookup is performed to retrieve data, and the value is returned from the first node that responds.
The advantages of Kademlia include its low latency, efficient routing mechanism, and resistance to certain types of attacks. However, Kademlia can be susceptible to Sybil and Eclipse attacks, undermining its performance and security.
Chord
Chord is a DHT protocol introduced by Ion Stoica and colleagues in 2001. It is based on consistent hashing, which ensures a balanced distribution of keys and provides fault tolerance. The key features of Chord are:
a. NodeID and Key Space: Chord assigns each node and key a unique identifier (NodeID and KeyID) in a circular space called the Chord ring. The clockwise distance between their NodeIDs determines the distance between nodes.
b. Finger Table: Each node maintains a finger table with entries pointing to successor nodes at exponentially increasing distances around the Chord ring.
c. Lookup Algorithm: The lookup process follows the finger table entries to reach the successor node responsible for the target KeyID.
d. Data Storage and Retrieval: Data is stored as key-value pairs on the successor node responsible for the KeyID. Retrieval follows the same lookup process as in Kademlia.
Chord offers efficient routing and load balancing, but network churn can affect its performance (frequent joining and leaving of nodes). Additionally, it may be vulnerable to Sybil and Eclipse attacks.
Pastry
Pastry, proposed by Antony Rowstron and Peter Druschel in 2001, is another DHT protocol similar to Chord but uses prefix-based routing. Its main features are:
a. NodeID and Key Space: Pastry, like Chord, assigns unique NodeIDs and KeyIDs in a circular space.
b. Routing Table: Each node maintains a routing table with multiple levels representing a different prefix length. The table entries store the contact information of nodes with matching prefixes.
c. Leaf Set: Besides the routing table, each node maintains a leaf set containing its closest neighbours in the circular space.
d. Lookup Algorithm: The lookup process uses the routing table and leaf set to route messages towards nodes with increasingly longer prefix matches to the target KeyID.
e. Data Storage and Retrieval: Data is stored in key-value pairs on the k closest nodes to the KeyID. Retrieval follows a similar lookup process as Kademlia and Chord.
Pastry provides efficient routing and scalability and can handle network churn effectively. However, it may be vulnerable to Sybil and Eclipse attacks, like Kademlia and Chord.
Comparison and Conclusion
Kademlia, Chord, and Pastry are three well-known DHT algorithms that offer unique approaches to distributed key-value storage and retrieval. Here is a comparison of their main properties:
- Routing Mechanism: Kademlia uses the XOR metric, Chord uses consistent hashing, and Pastry uses prefix-based routing. These mechanisms contribute to their efficient routing capabilities and logarithmic state complexity.
- Routing Table Structure: Kademlia employs k-buckets, Chord uses finger tables, and Pastry uses multi-level routing tables and leaf sets. These data structures help maintain network information and facilitate the lookup process.
- Fault Tolerance: All three algorithms provide fault tolerance through replication, storing data on multiple nodes to ensure availability despite node failures.
- Security: Kademlia, Chord, and Pastry are susceptible to Sybil and Eclipse attacks. Additional security mechanisms, such as secure routing protocols and identity verification, are required to address these vulnerabilities.
- Applications: These DHT algorithms are widely used in P2P networks, such as file-sharing systems (e.g., BitTorrent), content distribution networks (e.g., Coral CDN), and domain name systems (e.g., OpenDHT).
In conclusion, Kademlia, Chord, and Pastry are powerful DHT algorithms, each offering distinct advantages and facing specific challenges.
When selecting a DHT for a particular application, it is essential to consider the system's specific requirements, such as routing efficiency, fault tolerance, and security.
Happy coding!
Follow me on Medium, LinkedIn, and Twitter.
All the best,
Luis Soares
CTO | Head of Engineering | Go lang Enthusiat | Blockchain Engineer | Web3 | Cyber Security
#distributed #hash #table #dht #algorithm #kademlia #chord #pastry #routingtable #softwaredevelopment #softwareengineering #backend #development #softwaredesign



