Implementing a Distributed Hash Table (DHT) in Golang
Distributed Hash Tables (DHTs) provide a decentralized, fault-tolerant method for storing and retrieving data in a distributed network.
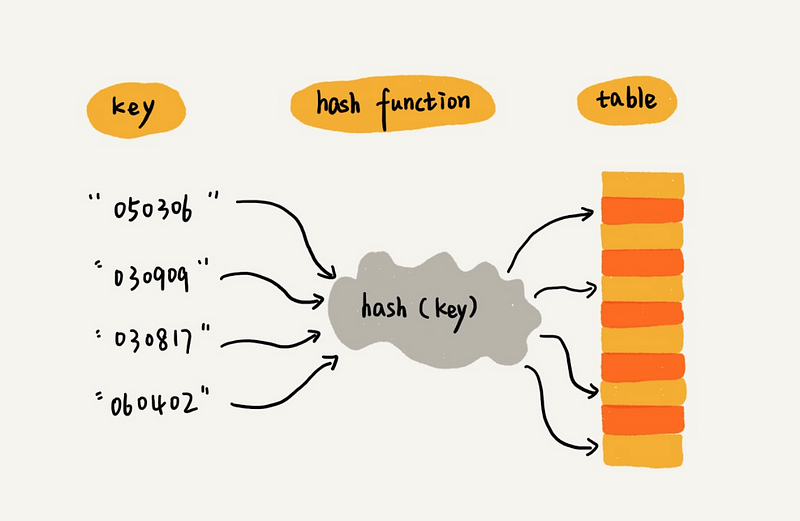
Distributed Hash Tables (DHTs) provide a decentralized, fault-tolerant method for storing and retrieving data in a distributed network.
In this article, I will provide some code examples to help you to implement a DHT in Go (Golang).
Stay tuned!
What is a Distributed Hash Table?
A Distributed Hash Table (DHT) is a decentralized data structure that allows nodes in a distributed network to store and retrieve key-value pairs efficiently.
Each node in the network is responsible for a small portion of the overall dataset, and nodes communicate with one another to locate the data associated with a given key.
DHTs in Blockchain
In a blockchain, transactions and data are stored in blocks linked together to form a chain. Each block contains a list of transactions and a reference to the previous block.
In decentralized networks like blockchain, nodes often need to locate specific blocks or transactions.
DHTs allow for efficient network querying, enabling nodes to locate the desired data quickly.
This is particularly useful in blockchains, as it minimizes the need for every node to store a full copy of the entire blockchain, making the network more scalable and efficient.
Example: A Simple DHT in Go
Now let’s create a simple DHT using Go.
First, we’ll define a basic structure to represent the DHT and its nodes:
package main
import (
"crypto/sha256"
"encoding/hex"
"fmt"
"sync"
)
type Node struct {
id string
data map[string]string
network *DHT
}
type DHT struct {
nodes []*Node
lock sync.RWMutex
}
func NewDHT() *DHT {
return &DHT{
nodes: make([]*Node, 0),
lock: sync.RWMutex{},
}
}Here, the DHT the structure contains a slice of pointers to Node structures, representing the nodes in the network.
The Node structure has an ID, a data map, and a reference to the DHT.
Next, we’ll create functions to add nodes to the DHT and hash keys:
func (dht *DHT) AddNode(node *Node) {
dht.lock.Lock()
defer dht.lock.Unlock()
dht.nodes = append(dht.nodes, node)
node.network = dht
}
func hashKey(key string) string {
hash := sha256.New()
hash.Write([]byte(key))
return hex.EncodeToString(hash.Sum(nil))
}Now, we’ll implement the functions to store and retrieve key-value pairs:
func (node *Node) Store(key, value string) {
hashedKey := hashKey(key)
node.data[hashedKey] = value
}
func (node *Node) Retrieve(key string) (string, bool) {
hashedKey := hashKey(key)
value, ok := node.data[hashedKey]
return value, ok
}Finally, we can create a main function to demonstrate the usage of our DHT:
func main() {
dht := NewDHT()
nodeA := &Node{id: "Node A", data: make(map[string]string)}
nodeB := &Node{id: "Node B", data: make(map[string]string)}
dht.AddNode(nodeA)
dht.AddNode(nodeB)
key := "example-key"
value := "example-value"
// Store the key-value pair in Node A
nodeA.Store(key, value)
// Retrieve the value from Node B
retrievedValue, ok := nodeB.Retrieve(key)
if ok {
fmt.Printf("Value retrieved from Node B: %s\n", retrievedValue)
} else {
fmt.Println("Failed to retrieve value from Node B")
}
// Retrieve the value from Node A
retrievedValue, ok = nodeA.Retrieve(key)
if ok {
fmt.Printf("Value retrieved from Node A: %s\n", retrievedValue)
} else {
fmt.Println("Failed to retrieve value from Node A")
}
}In this example, we create a simple DHT with two nodes, nodeA and nodeB.
We store a key-value pair in nodeA, and then attempt to retrieve the value from both nodes.
In this basic implementation, the value can only be retrieved from the node where it was stored.
To create a more advanced DHT, you would need to implement a routing algorithm to locate the appropriate node responsible for a given key and ensure that data is uniformly distributed across the network.
I wrote about the three most commonly used algorithms in this article: Kademlia, Chord, and Pastry.
Happy coding!
Follow me on Medium, LinkedIn, and Twitter.
All the best,
Luis Soares
CTO | Head of Engineering | Go lang Enthusiat | Blockchain Engineer | Web3 | Cyber Security
#go #golang #goprogramming #language #distributed #hash #table #dht #algorithms #routingtable #softwaredevelopment #softwareengineering #backend #development #softwaredesign #network #data #share #help



