Developing eBPF Hooks: First Steps
eBPF is a powerful Linux kernel technology that creates highly efficient and flexible hooks into the kernel, enabling users to develop…
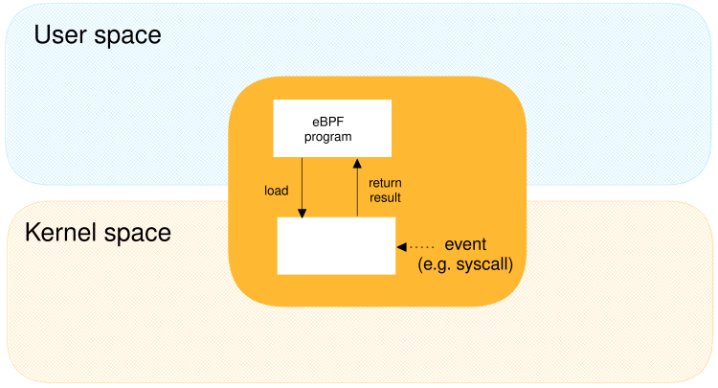
eBPF is a powerful Linux kernel technology that creates highly efficient and flexible hooks into the kernel, enabling users to develop custom tracing, networking, and security tools.
In this introductory guide, we’ll cover the key aspects of developing eBPF hooks, including an overview of eBPF, its tools, and code snippets to help you get started.
Let’s dive in!
Understanding eBPF
eBPF Basics
eBPF is an extension of the original BPF (Berkeley Packet Filter) and is a highly versatile in-kernel virtual machine.
eBPF programs are written in a restricted C-like language, compiled into eBPF bytecode, and then executed in a sandboxed environment within the Linux kernel.
eBPF offers a safe, efficient, and powerful way to instrument and extend kernel functionality.
eBPF Hooks
eBPF hooks are the points in the kernel where eBPF programs are attached, allowing them to be executed in response to specific events.
There are several types of eBPF hooks, including:
- kprobes: Dynamic kernel probes for tracing kernel functions
- uprobes: User space probes for tracing user space application functions
- tracepoints: Static probes for tracing specific kernel events
- XDP (eXpress Data Path): High-performance packet processing in the kernel
- cgroup-bpf: Hooks for applying eBPF programs to cgroups
Tools for Developing eBPF Hooks
LLVM/Clang
LLVM and Clang are essential tools for compiling eBPF programs. Clang is a C language compiler part of the LLVM project and compiles eBPF programs into bytecode.
BCC (BPF Compiler Collection)
BCC is a toolkit for creating, testing and debugging eBPF programs. It includes libraries, header files, and tools for writing eBPF programs in C and Python.
bpftool
bpftool is a command-line utility for managing eBPF programs and maps. It provides functions to load, unload, and manage eBPF programs in the kernel.
libbpf
libbpf is a library for loading and managing eBPF programs and maps. It provides a C API for working with eBPF and simplifies the process of working with eBPF objects.
eBPF Program Example: Counting Syscalls
The following eBPF program counts the number of syscalls made by processes:
#include <uapi/linux/ptrace.h>
#include <linux/sched.h>
BPF_HASH(syscall_count, u32);
int count_syscalls(struct pt_regs *ctx) {
u32 pid = bpf_get_current_pid_tgid();
u64 *count = syscall_count.lookup(&pid);
if (!count) {
u64 init_val = 1;
syscall_count.update(&pid, &init_val);
} else {
(*count)++;
syscall_count.update(&pid, count);
}
return 0;
}Compiling an eBPF Program
To compile an eBPF program, use Clang with the appropriate flags:
clang -O2 -target bpf -c my_ebpf_program.c -o my_ebpf_program.oAttaching the Syscall Counting eBPF Program with BCC
In this example, we’ll use BCC to load and attach the syscall counting eBPF program to a kprobe on the `__x64_sys_execve` kernel function, using Python:
from bcc import BPF
# Load eBPF program from source file
b = BPF(src_file="syscall_count.c")
# Attach eBPF program to a kprobe
b.attach_kprobe(event="__x64_sys_execve", fn_name="count_syscalls")
# Print syscall counts every 5 seconds
while True:
print("=== Syscall Counts ===")
for k, v in b["syscall_count"].items():
print(f"PID {k.value}: {v.value} syscalls")
time.sleep(5)Debugging and Performance Tuning
Debugging eBPF programs can be challenging due to their in-kernel execution. However, several techniques can help:
- Use
printk-like debugging withbpf_trace_printkto print messages from your eBPF program to the trace buffer. - Use BCC’s Python API for attaching probes and printing debug information.
- Leverage tools like
bpftoolmanaging, inspecting, and verify eBPF programs and maps.
Performance Tuning
Performance is critical to eBPF programs, as they are executed in the kernel context.
Here are some tips for optimizing eBPF program performance:
- Minimize loops and branches in your eBPF code, as they may increase overhead.
- Optimize data structures and use efficient algorithms.
- Use the Least Recently Used (LRU) eviction policy in BPF maps to prevent uncontrolled growth and memory consumption.
- Utilize hardware offloading for networking-related eBPF programs.
I hope this quick intro to eBPF helps you to get a bit familiarized with eBPF hooks basic concepts and implementation.
Stay tuned for new posts with a more in-depth hands-on implementation to take you further in the eBPF hooks journey.
Happy coding!
Follow me on Medium, LinkedIn, and Twitter.
All the best,
Luis Soares
CTO | Head of Engineering | Go lang Enthusiat | Blockchain Engineer | Web3 | Cyber Security
#eBPF #linux #kernel #hooks #bytecode #virtualmachine #LLVM #compiler #application #softwaredevelopment #softwareengineering #backend #development #softwaredesign #security #technology #networking



