Clickjacking Attacks: A Sneaky Threat
Clickjacking, or User Interface Redressing, is a cyberattack in which an attacker tricks the user into clicking on concealed elements on a…
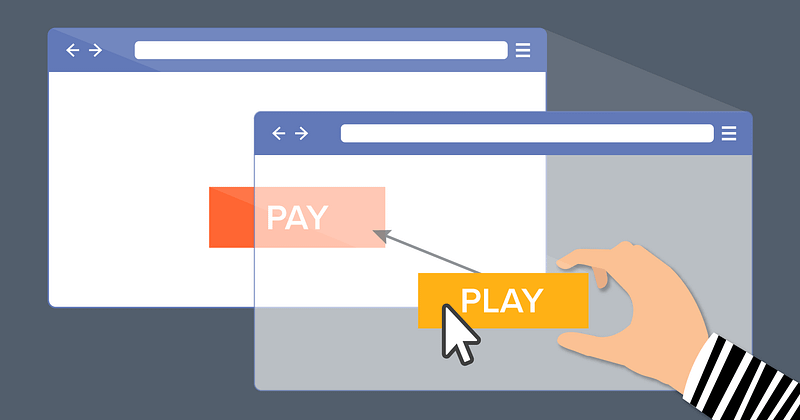
Clickjacking, or User Interface Redressing, is a cyberattack in which an attacker tricks the user into clicking on concealed elements on a web page.
The attacker manipulates the visual layout of a legitimate web application, overlaying elements in a manner that leads the user to perform actions they did not intend to.
The consequences of a clickjacking attack can range from simple annoyance to severe, including theft of sensitive information, unauthorized actions on the user’s behalf, and the installation of malware.
How Does Clickjacking Work?
At the heart of clickjacking lies the manipulation of web page layers.
Attackers create a malicious web page containing an invisible iframe, essentially an embedded HTML document within the main document.
This invisible iframe is then loaded with the target web application’s content. The attacker then overlays carefully crafted, enticing content on top of the iframe, which prompts the user to interact with the page.
Users who click on the overlaid content interact with the invisible iframe and unknowingly perform actions on the legitimate web application.
This way, attackers can deceive users into clicking on sensitive elements such as ‘like’ buttons, ‘share’ links, and download buttons for malware.
Preventing Clickjacking Attacks
The following security measures might help you protect your organization:
- Content Security Policy (CSP): Implement a CSP to restrict the sources of content that can be embedded within your web application. This can prevent an attacker from loading your content in a malicious iframe.
- X-Frame-Options (XFO) header: Use the XFO header in your web application’s HTTP response to control whether or not your content can be embedded within an iframe. The XFO header has three options: DENY, SAMEORIGIN, and ALLOW-FROM. The DENY option prevents your content from being embedded in any iframe, while SAMEORIGIN allows it only when the parent site is the same as the embedded content.
- Frame-ancestors directive: As an alternative to the XFO header, you can use the frame-ancestors directive within your CSP. This directive allows you to specify a whitelist of sources permitted to embed your content.
- JavaScript frame-busting techniques: Employ frame-busting scripts that detect when your web page is embedded within an iframe and force the browser to navigate away or break out of the frame.
- User education: Educate your users about clickjacking and encourage them to be cautious when clicking suspicious or unknown links. This can help reduce the likelihood of them falling victim to such attacks.
Follow me on Medium, LinkedIn, and Twitter.
All the best,
Luis Soares
CTO | Head of Engineering | Cyber Security | Blockchain Engineer | NFT | Web3 | DeFi | Data Scientist
#cyber #cybersecurity #cyberattack #threat #security #devsecops #owasp10 #owasp #vulnerability #hacker #hacking #prevention #clickjacking



