
Technical Threat Intelligence
Technical Threat Intelligence refers to the information and data organisations collect and analyse to identify, understand and predict…

Technical Threat Intelligence refers to the information and data organisations collect and analyse to identify, understand and predict…

Cryptography is the study of secure communication and is used to protect information from unauthorised access. Cryptography is used in…
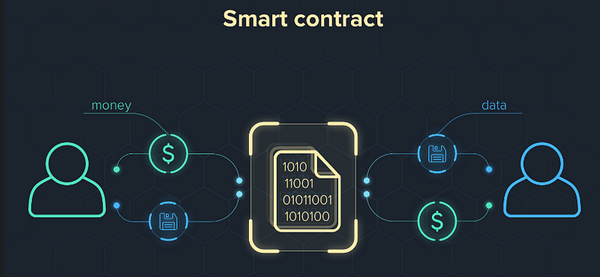
Smart contracts are self-executing programs that run on blockchain platforms like Ethereum. They can be used to automate a variety of…

Zero Trust is a security concept based on assuming that all devices, users, and systems inside and outside of an organization’s network are…

Open source vulnerability databases are collections of information about known security vulnerabilities in open source software. They are…
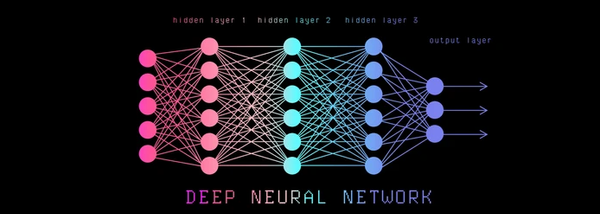
Neural networks are artificial intelligence modelled after the human brain’s structure and function. They are used for a wide range of…
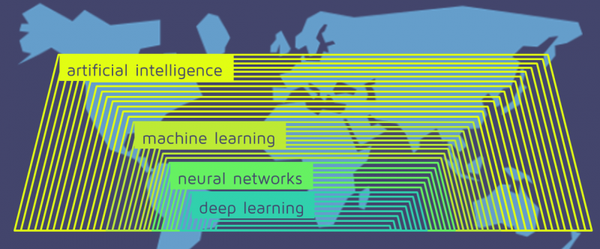
Deep Learning is a subfield of machine learning that uses artificial neural networks with multiple hidden layers to model and solve complex…
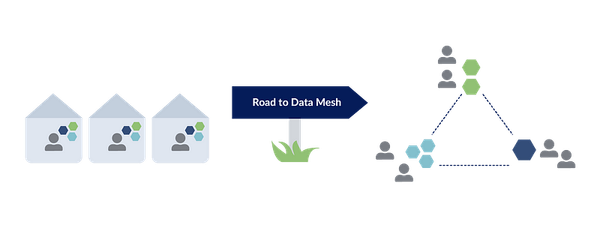
Data Mesh is an architectural pattern that prioritizes data management as a first-class citizen in organizations. It aims to address the…

Data is an essential tool for understanding customer behaviour. By analyzing customer data, businesses can understand who their customers…
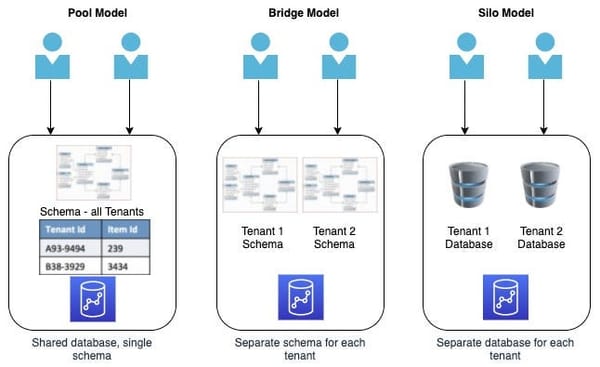
A multi-tenant application is a software designed to serve multiple customers (tenants) using a single instance of the application. This…
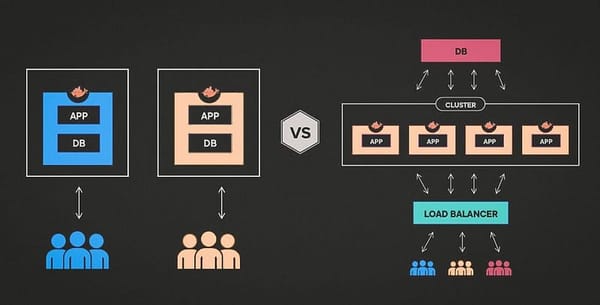
Multi-tenant architecture is a software architecture that enables multiple tenants to share a single instance of a software application…

DevSecOps is a methodology for integrating security practices into the software development process. It is an extension of the Agile and…