
The pass-the-hash attack explained
A “hash” is a mathematical representation of data, often used as a security measure to ensure that sensitive information, such as…

A “hash” is a mathematical representation of data, often used as a security measure to ensure that sensitive information, such as…
A firewall is a crucial network security tool that helps protect computers and networks from malicious attacks. It acts as a barrier…

Forward secrecy-based protocols, also known as Perfect Forward Secrecy (PFS), are a class of cryptographic protocols that aim to provide…

Smart contract obfuscation refers to the process of hiding or encrypting the code of a smart contract, making it difficult for an attacker…
A clustering algorithm is a popular technique in big data analytics that involves grouping similar data points together. The main goal of…
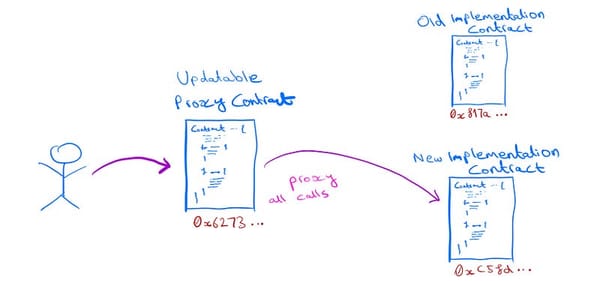
Smart contracts have revolutionized the way we interact with the blockchain. They allow for the trustless execution of agreements between…
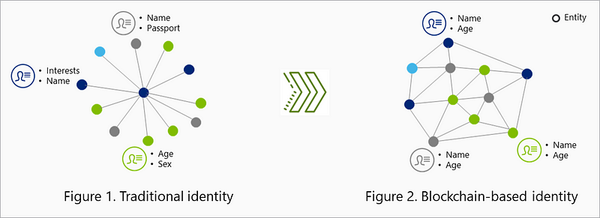
Decentralized identities, or DIDs for short, are a new way of managing digital identities that puts users in control of their data. Instead…

Web applications are ubiquitous in today’s digital age, and with that comes an increasing need to secure them against various security…

Datafication refers to the process of transforming various types of data into a digital format, which can be easily analyzed and used to…

A digital immune system is a combination of hardware and software tools that work together to prevent, detect, and respond to cyber…

Hyperautomation is a combination of technologies that allows businesses to automate and streamline their processes, thereby increasing…
Buffer overflow vulnerability is a type of security vulnerability that can allow an attacker to execute malicious code on a system or gain…