
Implementing a ChatGPT Plugin in Python: A Step-by-Step Guide
To demonstrate how to create a ChatGPT plugin, let’s assume we want to build a plugin that allows users to receive weather updates based on…

To demonstrate how to create a ChatGPT plugin, let’s assume we want to build a plugin that allows users to receive weather updates based on…

EIP-712 is a standardized method for structuring and signing human-readable and machine-verifiable data. This method allows users to…

The concept of Defense in Depth has its roots in military strategy, dating back to the Roman Empire.
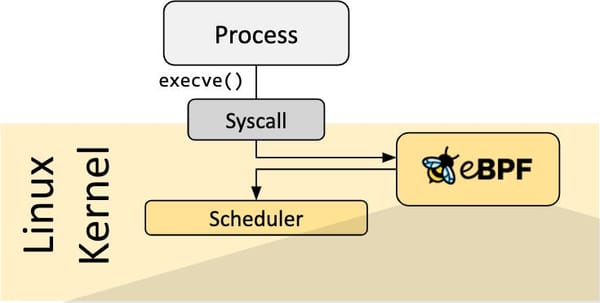
Extended Berkeley Packet Filter, or eBPF, is a technology in the Linux kernel that has gained significant attention in recent years.

Since its launch in 2015, WebAssembly has gained significant traction in the developer community and has proven to be a game-changer for…

In the digital world, trust is of paramount importance. Non-repudiation is a security feature that plays a vital role in achieving this.
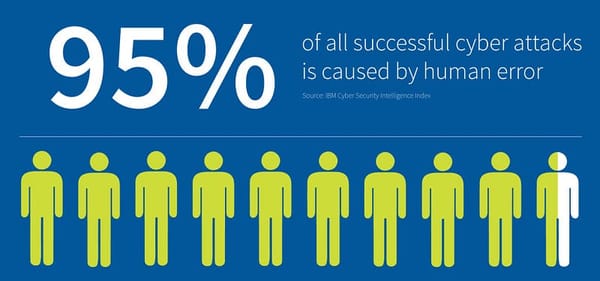
While many organizations invest heavily in cutting-edge security measures, the human factor remains a significant vulnerability in…

Secure Sockets Layer (SSL) certificates are an essential component of internet security, providing encryption and authentication for…

A Virtual Private Network (VPN) is a powerful tool that helps maintain privacy and security while browsing the internet. It encrypts and…

Big Data has been a buzzword in the tech industry for quite some time, with organizations increasingly leveraging data-driven insights to…

As the world of machine learning continues to evolve, new technologies and methodologies emerge to cater to different use cases and…

Day Zero attacks are cyber attacks that exploit a vulnerability or flaw in a system or software before it is discovered or patched by the…