
Malware Analysis 101: Techniques & Tools
Malware analysis is an essential cybersecurity practice to examine malicious software to uncover its purpose, functionality, and potential…

Malware analysis is an essential cybersecurity practice to examine malicious software to uncover its purpose, functionality, and potential…

Secure Access Service Edge (SASE) is a new network architecture model that aims to simplify and enhance security, performance, and…
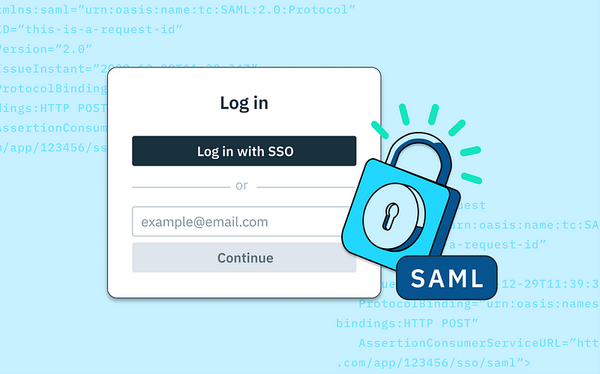
The Security Assertion Markup Language (SAML) is an XML-based standard for exchanging authentication and authorization data between…
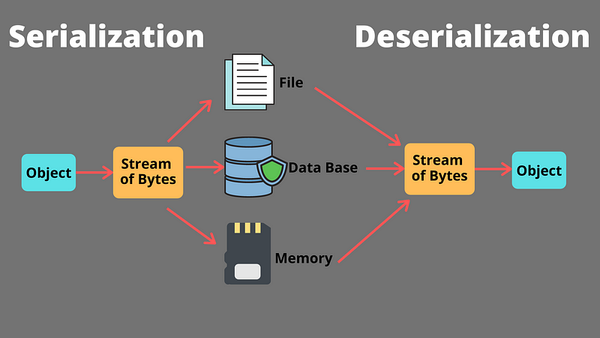
Insecure deserialization is a prominent security vulnerability that occurs when an application deserializes untrusted or malicious data…

Kubernetes Ingress is a collection of rules that govern how external traffic is routed to services within a Kubernetes cluster. It enables…
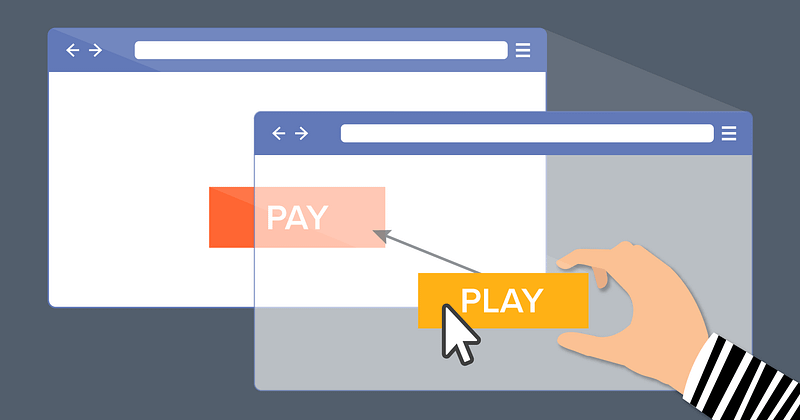
Clickjacking, or User Interface Redressing, is a cyberattack in which an attacker tricks the user into clicking on concealed elements on a…

A Cloud Access Security Broker (CASB) is a software tool or service that sits between an organization’s on-premises infrastructure and the…

Hardware Security Modules (HSMs) are dedicated cryptographic devices designed to provide robust security for sensitive digital information…

In this article, we will explore how to implement a simple fraud detection system in Python using machine learning techniques.
The R programming language has become a popular choice for statisticians, data scientists, and researchers across the globe.

Outlier detection is a critical step in the data science process. Outliers are data points that diverge significantly from the rest of the…

GraphQL is a robust query language and runtime that allows developers to request and manipulate data flexibly. Its flexibility, though, can…