7 Tips for Preventing Insecure Deserialization Vulnerability
Insecure deserialization is a prominent security vulnerability that occurs when an application deserializes untrusted or malicious data…
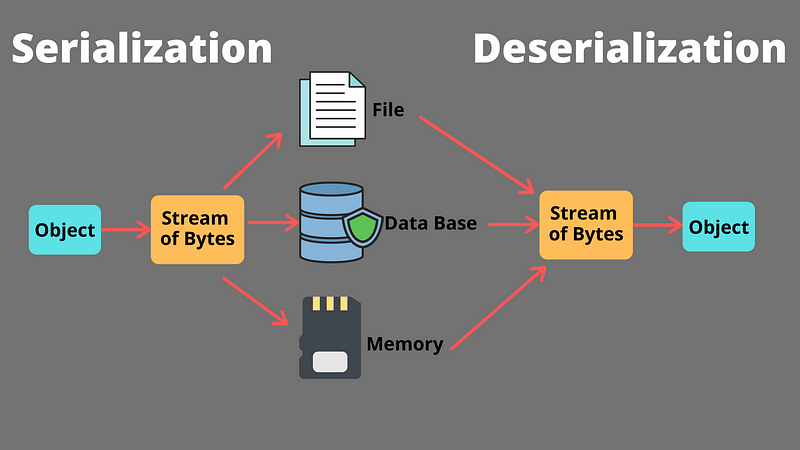
Insecure deserialization is a prominent security vulnerability that occurs when an application deserializes untrusted or malicious data without proper validation.
For instance, when an application deserializes data from an untrusted source, an attacker could potentially craft a malicious serialized payload that, when deserialized by the application, results in the execution of arbitrary code or modification of the application's data, leading to unauthorized access, data manipulation, or even remote code execution.
Here are seven tips to help prevent insecure deserialization through best practices in application security:
- Validate and Sanitize Input: Always validate and sanitize data before deserializing it. Implement strict input validation checks to ensure that only legitimate data is accepted. Use allow-lists and regular expressions to filter out potentially harmful data and limit the accepted data types.
- Use Secure Serialization Mechanisms: Avoid using serialization mechanisms known to be vulnerable, such as binary serialization or XML deserialization with DTD processing enabled. Opt for secure serialization methods, such as JSON, which are less prone to deserialization attacks.
- Implement Cryptographic Controls: Encrypt serialized data to ensure an attacker cannot modify it without the appropriate decryption key. Use a robust encryption algorithm like AES and manage keys securely.
- Use Object Signing: Sign serialized objects using digital signatures to ensure the integrity and authenticity of the data. When deserializing data, verify the signature to ensure that the data has not been tampered with.
- Restrict Deserialization to Safe Types: Limit deserialization to specific, known-safe types if possible. This can help prevent attackers from exploiting deserialization vulnerabilities to execute arbitrary code or manipulate application data.
- Implement the Least Privilege Principle: Ensure that the application runs with the least possible privileges, limiting the potential damage in case of a successful deserialization attack. Additionally, segregate and compartmentalize application components to minimize the potential attack surface.
- Keep Software Up to Date: Regularly update your application's software, libraries, and frameworks to benefit from the latest security.
Developers can mitigate risks and build more secure applications by understanding their low-level mechanics and implementing prevention techniques.
Follow me on Medium, LinkedIn, and Twitter.
All the best,
Luis Soares
CTO | Head of Engineering | Cyber Security | Blockchain Engineer | NFT | Web3 | DeFi | Data Scientist
#cyber #cybersecurity #cyberattack #threat #security #devsecops #owasp10 #owasp #vulnerability #hacker #hacking #prevention #deserialization



